Public Keys
Anthology Inc. has implemented a new process to secure sending and receiving of files to and from File Transfer Protocol (FTP) and Azure Cloud Storage. This newly implemented process will use the OpenPGP encryption standard that uses public key cryptography.
Learn more about OpenPGP
The process will enable the use of public/private key flow when transmitting files with data that could include personal identifiable information (PII) or secondary personal identifiable information (SPII). Due to this being a new process, some initial setup and configuration work will be required. This guide will detail the initial setup process and how the public key will be used in the Staff Portal for encryption purposes.
A high-level overview of the new public/private key process is outlined below.
-
The recipient (client) of the file(s) generates two keys: public key and private key.
-
The public key is used for encryption.
-
The private key is used for decryption.
-
-
The recipient gives the public key to the sender.
-
The sender uses the public key to encrypt the file.
-
The sender sends the encrypted file to the recipient.
-
The recipient decrypts the file with his private key.
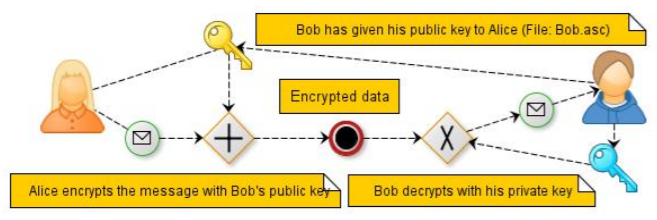
Example: Bob (recipient) uses a software to generate a public and private key. Bod then uploads his public key, so Alice (sender) can encrypt files that she sends over to Bob’s FTP location.
Setup
The first step in the setup process is generation and management of new public and private keys. It is very important that once the keys have been generated that they are safeguarded and a standard operating procedure is developed. The ownership and management of the public and private key generation is the sole responsibility of the client. Anthology Inc. will not be able to retrieve or access public keys unless given to us by the client. Your private key will remain internal and should not be shared outside of your organization or with Anthology Inc..
There are multiple free tools that are available to generation and manage public and private keys. For purposes of this guide, screenshots and steps will be taken using the Kleopatra 3.0.2 -gpg4win-3.0.3 software (Windows).
-
https://www.gpg4win.org/download.html - Windows
-
https://scand.com/products/wingpg/ - Windows
-
https://gpgtools.org/ - macOS
Important: Client management of the public and private key is crucial. Please ensure your private key is safeguarded, as files will be encrypted from EP using the public key associated with the private key. The private key will be stored on the hard drive of the computer in which the keys were generated, so if this computer becomes damaged or lost. The process of decrypting files will be lost and EP will not be able to generate encrypted files again. Please export your private key and store it on an external drive and then re-import it on to a new computer.
Download Software
Download one of the software(s) listed above or your preferred software aligning with the GPG tools. Please be sure to select the .ASC extension as one of your selections when downloading the new tool.
After successfully downloading your new software. Please complete the following steps to generate and manage public and private key(s)
-
Open Kleopatra.
-
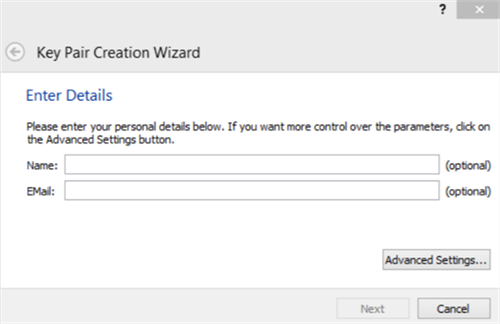
Select New Key Pair. The Key Pair Creation Wizard box will display and require the following. The New Key Pair Wizard will generate a public and private key upon saving.
-
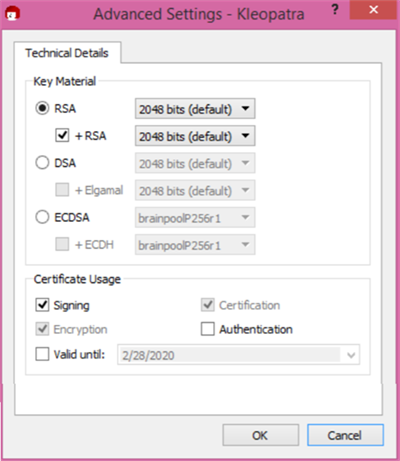
Please enter your personal details below. Select Advanced Settings to review additional parameters.
- Name
- Key Material
- RSA (2048 bits default)
- Certification Usage
- Signing
- Certification
- Encryption
-
Valid Until (if checked, an expiration date will be required and set for your public and private key)
Important: If an expiration date is set for your public key and Anthology Inc. is not made aware prior to the expiration. Files sent during this period will be lost and cannot be re-generated. It is important to ensure EP has the most recent public key on file.
-
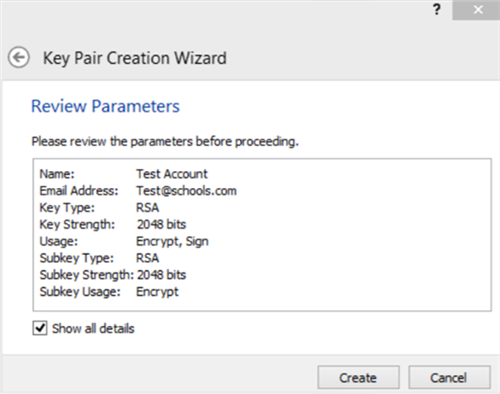
Select OK. The Review Parameters screen will be displayed. Be sure to select Show all details check box. After review, select the Create button to proceed.
-
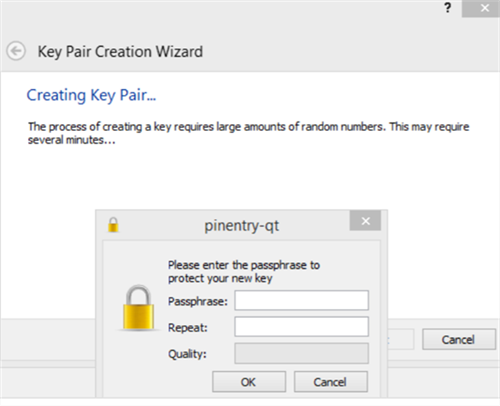
Creating Key Pair will begin and you will be prompted to enter a passphrase to protect your new key.
-
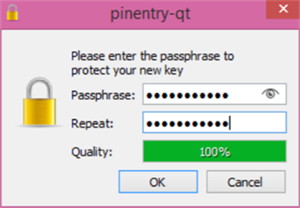
The Quality of the passphrase will be monitored and you will be prompted to re-enter should it not meet the strong requirements standard.
-
Select OK.
-
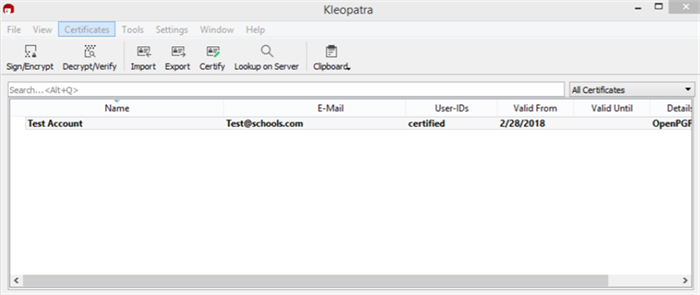
The main Kleopatra page will be displayed after successful generation of the key pair.
-
Select the Export option located in the menu header.
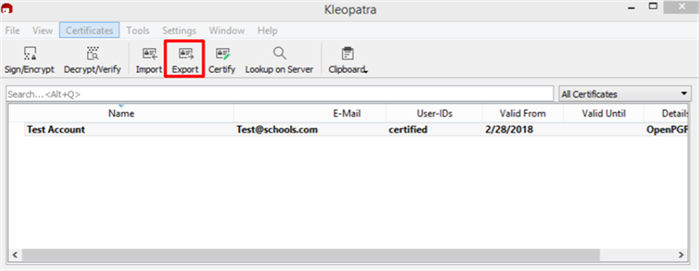
-
The Export Certificates box will appear. Update the File Name (if needed) and Save the public key to preferred location.
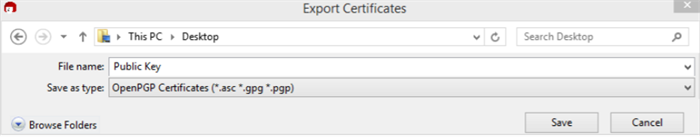
-
The Certificate Import Result (this will also appear if the saved file is selected) box will appear and display the processed, imported, and unchanged statuses.
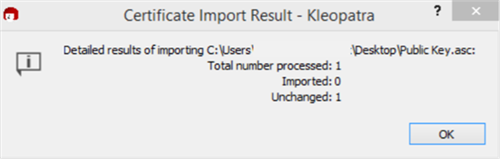
-
Select OK. Proceed to the next step. See Storage of Public Key
Storage of Public Key
The second step in the setup process is to store the newly created public key (or if the public key changes over time) in the Staff Portal. This enables Anthology Inc. to encrypt files sent from the Student Verification Staff Portal
A new page on the Staff Portal, located on the Administration menu that is provisioned by a new permission called Can Upload Public Keys. Anthology Inc. will only activate one public key at a time, we will capture activity history on changes made (i.e. new uploads, inactivation of key, successful uploads, failed uploads).
A user with appropriate permissions, can complete the following steps to upload a public key in the Staff Portal.
-
On the Administrators menu, under Site Administration, select Public Keys.
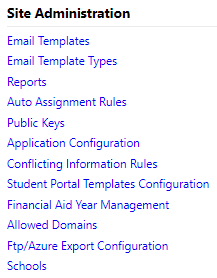
-
The Public Key page will be displayed. Select the Browse button to locate your public key file. Once successfully located, select Upload.
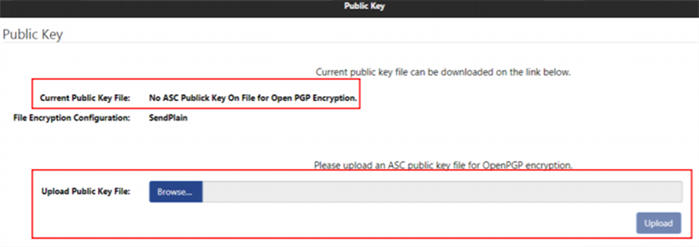
-
Please upload an ASC public key file for OpenPGP encryption.
-
Ensure successful upload before navigating away from the screen. The new file should reflect in the Current Public Key file area.
-
The Activity History will reflect below the Upload screen once the first upload occurs.
-
-
The new public key will reflect in the Current Public Key File section upon successful upload.
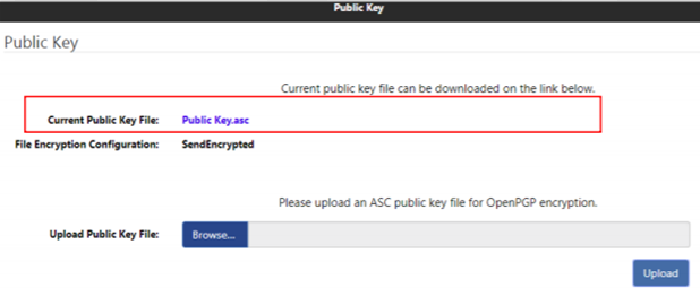
Change of Configuration Settings
The third step in the process is to change the configuration settings associated with the file transfer process. This step begins the adoption phase as it allows the customer the capability to set the format in which file(s) are transferred to FTP or email.
The available configuration setting (File Encryption Option) are as follows:
-
Send Plain (default value, current setting, sends only plain text files)
-
Send Plain and Encrypted (send plain text file and encrypted file)
-
This allows testing of the new encryption process, while still receiving the normal plain text file.
-
Send Encrypted (send only encrypted file)
Student Verification
The Student Verification (SV) Staff Portal has been updated to include the new encryption process. This portion of the guide will outline the areas with the application that now require the new public/private workflow.
Institutional Student Information Record (ISIR) Correction Files
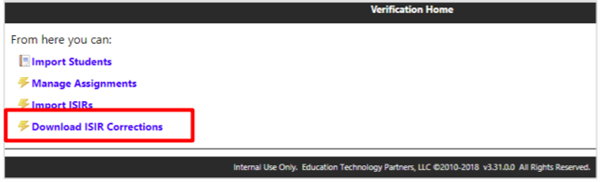
The Download ISIR Corrections option located on the Verification Homepage will begin to Send Plain and Encrypted or Encrypted after successful completion of the initial setup.
-
To begin downloading of ISIR correction file(s), log in to the Student Verification Staff Portal.
-
After successful login, navigate to the Download ISIR Corrections tab.
-
Select the check box for ISIR Correction(s) to download. Then proceed to select the Download ISIR Corrections.
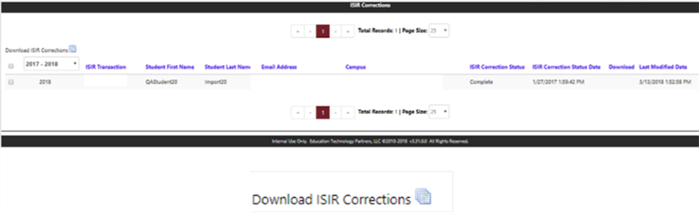
-
The CORRYYYYIN downloading box will be displayed. Select to Save in desired location.
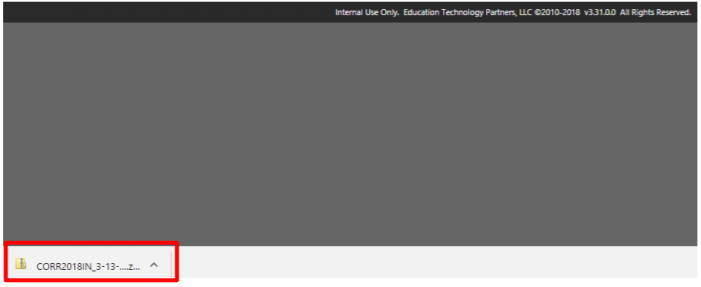
-
The newly downloaded folder will encompass two files when set to Send Plain and Encrypted.
-
A compressed (zipped) folder which requires the default MM password
-
An encrypted (Open PGP Binary) file using the public key (activated from the Associate Staff Portal)
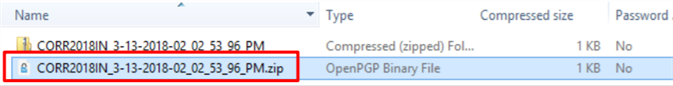
Note: The file name CORR2018_3-13-2018-02_02_0253_96PM is the normal plain text file and requires no password to open the file. The file name CORR2018_3-13-2018-02_02_0253_96PM.zip highlighted in the screen shot above is encrypted with the public key uploaded in the Student Verification Staff Portal.
-
-
Open the software that was used to generate the public and private key pair. Navigate to the Decrypt/Verify option located in the menu header.

-
Browse for the encrypted file located in the zipped folder.
Note: The easiest way to locate the encrypted file is to save it to your desktop or extract all out of the folder.
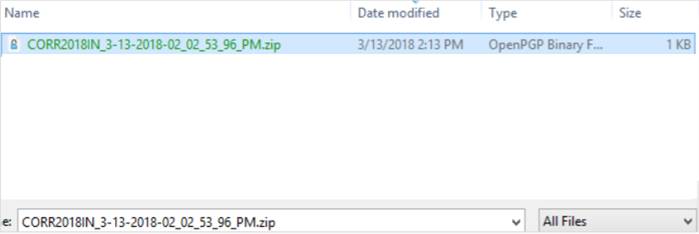
-
The Decrypt/Verify Files – Kleopatra operation box will appear and require the passphrase associated with the public/private key pair to begin the process.
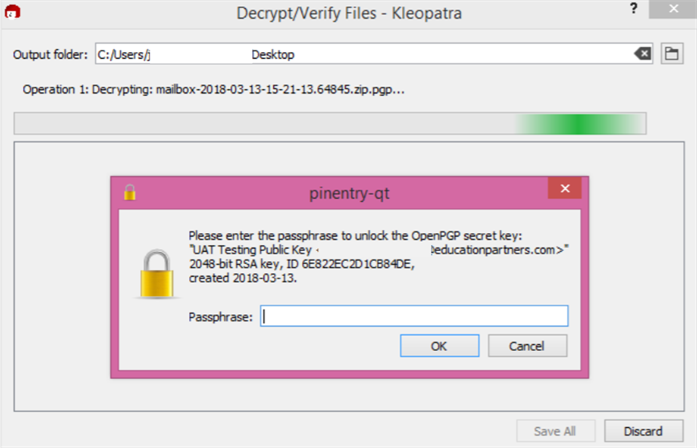
-
After successfully entry of the passphrase the decryption process will begin.
-
A confirmation will appear once the decryption process is complete.
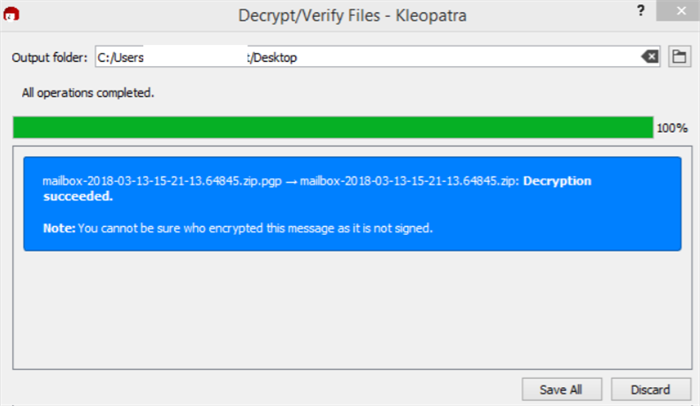
-
The decrypted file will appear in the saved location.
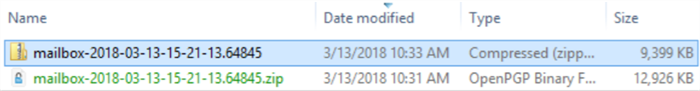
-
The message class file is available for processing as needed.
File Transfer Protocol Import Processor and Data Exporter Tool
The Student Verification Portal is configured with additional File Transfer Protocol (FTP) Import processing and Data Exporter tools. Review the following chart below to identify where the new encryption process has been implemented.
| Description | File Name Example |
|---|---|
| ISIR Verification Email Activity | {ClientCode}-IVEA-{CurrentDateTime}.txt {.pgp if encrypted} |
| ISIR Verification Required Document Statuses | {ClientCode}-IVDS-{CurrentDateTime}.txt {.pgp if encrypted} |
| ISIR Verification Statuses | {ClientCode}-IVS-{CurrentDateTime}.txt {.pgp if encrypted} |
| ISIR Correction files | CORR{FinancialAidYearLastTwoDigits}IN_{CurrentDateTime}.zip{.pgp if encrypted} |
Note: The second part of this implementation will be to encrypt files sent to Anthology Inc.. In this event the Student Import and ISIR Import Processor will be part of the new encryption process. Details of phase 2 are forthcoming.